- 27 March 2024
- Rob Fisher
In an era where our lives are increasingly reliant on digital technologies, the security of system-on-chip (SoC) devices has emerged as a major concern, particularly in consumer and Internet of Things (IoT) applications. An SoC integrates all the core components of a digital system into a single chip, offering a cost-effective, efficient solution for many consumer and IoT applications.
Consumer and IoT applications are used in virtually every aspect of modern life, from smart home devices and wearables to industrial automation and healthcare systems. While these innovations promise convenience, efficiency, and connectivity, they also expose users to unprecedented risks. The interconnected nature of these devices makes them susceptible to cyber threats ranging from data breaches and identity theft to unauthorised access and device manipulation.
Securing SoC devices is imperative for safeguarding sensitive data, such as personal information or paid-for content, and for maintaining the integrity of connected systems. A breach in SoC security can have far-reaching consequences, compromising not only individual users but also entire networks and infrastructures. Moreover, the proliferation of IoT devices amplifies the potential attack surface, as each interconnected device represents a potential entry point for malicious actors.
Given the critical role of SoC devices in consumer and IoT applications, addressing security concerns demands a multi-faceted approach. This entails integrating robust security mechanisms into the design and development processes, implementing stringent access controls and encryption protocols, and fostering collaboration among stakeholders to establish industry-wide standards and best practices.
SoC designers employ a variety of security mechanisms to ensure the integrity, confidentiality, and availability of systems; where these mechanisms are implemented at different levels, including hardware, firmware, and software. Here are some key security mechanisms commonly used in SoC design:
Root of Trust
A Root of Trust (RoT) serves as a foundational component essential for establishing and maintaining the integrity of the device. The RoT is a secure and trusted starting point from which the device's security mechanisms and operations are initiated and verified.
Often a physically separate device, the RoT typically consists of hardware, firmware, and software components designed to perform critical security functions, such as cryptographic operations, secure booting, and attestation. It forms the base upon which higher-level security features and protocols are built, ensuring that they can be reliably executed and protected from tampering or unauthorized access.
By establishing a trusted foundation and enforcing security measures from the ground up, the Root of Trust plays a pivotal role in the overall security of SoC devices.
Secure Boot
The secure boot process in a System-on-Chip (SoC) is a fundamental security mechanism designed to ensure that the device boots securely by verifying the integrity and authenticity of each component in the boot chain before allowing its execution. Secure boot is crucial for protecting against various threats that attempt to compromise the device's firmware or operating system during the boot sequence.
Starting with an immutable secured state, like a Boot Rom, and finishing with loading of a secure execution environment and user applications, the secure boot process establishes a chain of trust, verifying the integrity and authenticity of each subsequent stage of the boot process.
Trusted Execution Environments
A Trusted Execution Environment (TEE) is a logically isolated secure execution environment, where sensitive operations can be performed with a high degree of assurance regarding their integrity and confidentiality. For example: biometrics, payment clients, DRM clients, and user identity management. TEEs are typically implemented using a combination of hardware and software security mechanisms to create a logically protected enclave, without needing physically isolated hardware.
The combination of these elements and other functions such as True Random Number Generators (TRNG), cryptographic accelerators and secure debug make the foundation of SoC security system. An example secure system initialisation process is shown below.
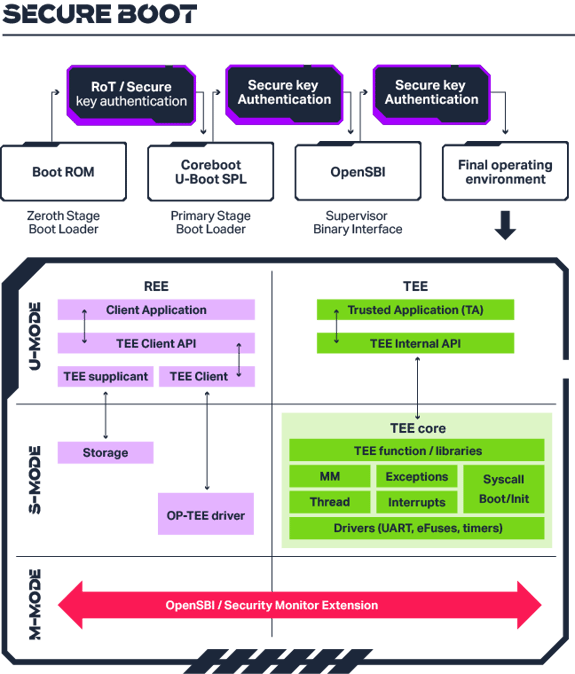
By combining these hardware and software-based security mechanisms, SoC designers aim to create a comprehensive security architecture that protects the device from a wide range of potential threats and vulnerabilities.
RISC-V
The RISC-V Privileged Architecture defines specific modes of execution which isolate Operating Systems (OS) from user applications. This coupled with Supervisor Domain Isolation, which isolates regions of memory and execution context for specific software domains, provides the foundation principles for the secure execution.
The Privileged Architecture defines the privilege levels, such as supervisor mode (S-mode), user mode (U-mode) and Machine Mode (M-mode). M-mode includes features like traps and event handling, which are crucial for implementing secure boot processes and handling security-related events.
The Supervisor Domain Isolation separates execution state and memory access for logically isolated software domains, allowing a Rich OS environment to operate alongside a Trusted Execution Environment (TEE) hosting trusted applications. This is enabled by a collection of extensions such as interrupt management (AIA), granular external and self-hosted debug, and access control mechanisms (PMP/PMA, Smsdid, Smsdia).
In addition, there are Cryptographic Extensions which include instructions for accelerating cryptographic operations, such as encryption and hashing, which are essential for securing data and communications. These extensions include instructions accelerating algorithms, like AES (Advanced Encryption Standard) and SHA (Secure Hash Algorithm) and, crucially, a set of constant-time instructions that mitigate against data-dependent timing attacks.
Ensuring integrity
Imagination’s Catapult CPU range builds on the ratified RISC-V profiles along with the above extensions to create an end-to-end security methodology that complements existing industry norms rather than creating a divergent strategy. Working as part of the RISC-V Software Ecosystem (RISE), Imagination is developing foundational open-source software to underpin RISC-V secure systems. For more information, visit us at Embedded World 2024 or contact our team.